This last week in October wraps up Cybersecurity Awareness Month, an annual observance now in its 18th year. Originally started by the National Cyber Security Division (within the Department of Homeland Security) and the nonprofit National Cyber Security Alliance, this significant month intends to raise awareness on the importance of cybersecurity in order for Americans and American-based businesses to have the resources they need to be safer and more secure online.

As we near the end of 2021, cybersecurity remains a critical issue across not only America, but the world. This past year alone, cybercriminals have attacked both technical and social vulnerabilities, taking advantage of the COVID-19 pandemic and the increase in remote work as a result. According to the 2020 FBI Internet Crime Report, the Internet Crime Complaint Center (IC3) received over 28,500 complaints related to COVID-19. Apart from financial fraud involving the federal CARES Act stimulus funds and Paycheck Protection Program (PPP), along with loans and increases in phishing schemes and bot traffic, there remains a continuous wave of worldwide ransomware and software supply chain attacks.
Phishing, a form of social engineering where criminals target human over technical vulnerabilities remains the most common attack performed by cybercriminals. In 2020, an astounding 6.95 million new phishing and scam webpages were developed, targeting the technology, finance, and retail sectors, riddled with themes such as COVID, gaming hacks, gift cards, and more.
While cybersecurity faces slowing budget growth, frustrated at-risk executives, and shifting regulatory focus, according to Gartner’s refreshed August 2021 report, “Why Today’s Cybersecurity Trends Fall Short in Reducing Risk,” cyber attacks still continue to soar. As companies gear up to thwart the onslaught of cyber threats and attacks and prepare these budgets, they should keep in mind the below “Top 3” list of challenges to consider for 2022.
1. The Social Engineering Threat
What may be surprising to some is the fact that many sources of corporate hacks, leaks, and breaches are not the work of sophisticated hacker “masterminds” utilizing the most advanced technical approaches, but are actually the result of simple social engineering attacks. Criminals engaging in social engineering are those who gain access to systems by manipulating the trust of users, who often aren’t aware anything has gone astray. It’s not usually until quite some time after that these risky actions are even noticed by individuals or teams, and by then it’s too late to get back to normal.
Social engineering threats use human psychology to achieve nefarious goals and are so common nowadays that enterprises and individuals alike have surely come across attempts online, or may have even fallen victim to one without realization. Further, social engineering attacks were the cause of some of the 15 biggest data breaches of the 21st century, including LinkedIn in 2021. An informative visualization to check out on this is here.
The three types of social engineering attacks to look out for into 2022 include:
Baiting, which refers to hackers leaving physical media somewhere for the target to easily find it, and/or making it possible for easy access to this media, and then relying on their natural curiosity to create a security breach. Online baiting also exists in the form of enticing advertisements or free downloads, both of which should be avoided by those seeking to keep their network safe.
Pretexting, which refers to a cybercriminal posing as an authority figure in an organization and proceeding to call employees to obtain private information such as addresses, security numbers, etc., and/or to establish identity. This scam can occur in several forms, including by phone, email, IM, and other communications. Individuals and businesses should always practice caution and be skeptical of communication attempts via numbers, accounts, or individuals they have not previously heard from before and never give information to someone that can’t be 100% verified as legitimate.
Phishing, which refers to the fraudulent practice of sending emails purporting to be from reputable companies in order to convince individuals to reveal personal information, such as passwords and credit card numbers (and as earlier stated, is the most common attack performed by cybercriminals). Phishing criminals will often send out hundreds or even thousands of these types of links across one organization, seeking just one person to fall for the hook. To fight these attempts, always verify any suspicious correspondence with the sender, preferably in a way that doesn’t expose any data. A quick and easy way to vet the communication is to check the exact sender details (many phishers will pose as a company name, but their email address will be completely different).
With all of the above in mind, it’s crucial to keep your cybersecurity software up-to-date, use email filtering processes, analyze suspected emails, educate employees about attacker tactics and remove all unnecessary administrative accounts.
To get even further ahead in social engineering attack prevention, many enterprises are seeking out Zero Trust, a security framework that requires all users – in and outside of the network – to be authenticated, authorized, and continuously validated for security configuration and posture before being allowed to maintain and or be granted access to applications and data. Zero Trust works under the assumption that there is no traditional network edge; that networks can be local, in the cloud, or a combination of both, with works in any locations and resources anywhere.
Zero Trust uniquely addresses the modern challenges of today’s business, including securing remote workers, hybrid cloud environments, and ransomware threats.
2. Societal Perception, Asking the Wrong Questions and Slowing Investments
Listed in the aforementioned Gartner report are the cybersecurity issues pertaining to societal perception, asking the wrong questions, and lowering related budgets. First, many enterprises share the incorrect point of view that cybersecurity is a technical problem and therefore best handled by technical people – and this line of thinking is usually dominated by fear, doubt, and uncertainty. This ultimately paves the way for poor decisions and lacking investments in cybersecurity. Additionally, as a result of the poor misunderstanding, unproductive questions come about regarding the real issues at hand, thus driving attention away from better understanding and investments.
Per Gartner, CIOs who are focused on IT cost optimization, finance, risk, and value to optimize risk and corporate performance should first, understand the business context of their organizations, and second, engage in research to build a business case and executive narrative to change how cybersecurity is treated in the organization. They should improve cybersecurity readiness by treating it as a choice and a business decision and thereby drive cybersecurity priorities and investments by using an outcome-driven approach balancing both risk and investment along with the needs to achieve desired business outcomes.
A considerable challenge that organizations face is determining the accurate amount of cybersecurity protection and investment. It is important that they instead shift to measuring levels of protection to guide investment. Some organizations will engage in outcome-driven metrics (ODM) for technology risk, which is an abstraction of tools, people, and processes to reflect how well an organization is protected, not how it is protected. ODM can be used to ensure more effective governance over cybersecurity priorities and investments while creating the language necessary to have meaningful business-focused conversations with executives and stakeholders.
3. Ransomware Attacks
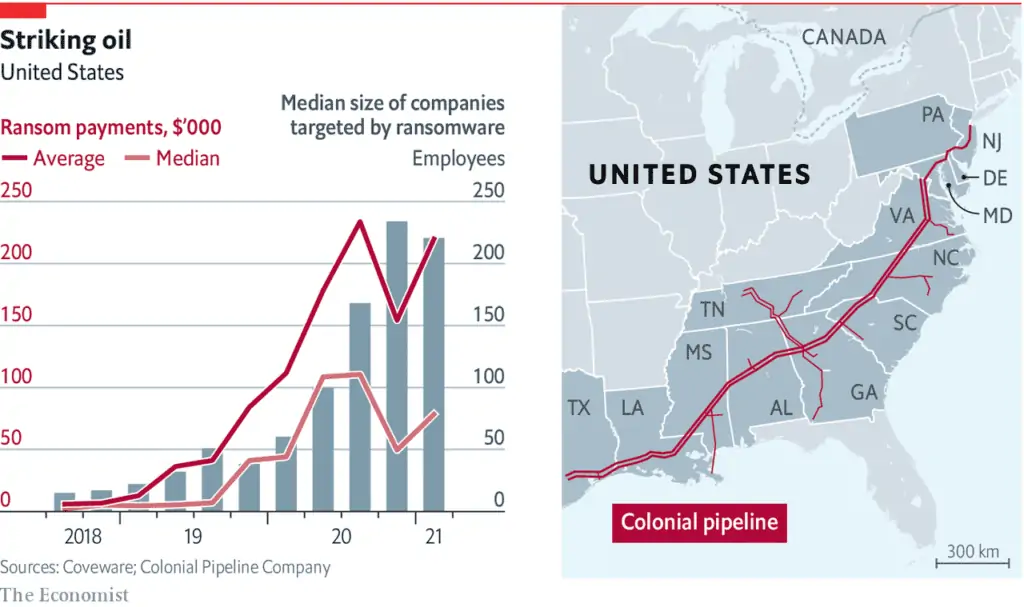
According to ThreatPost.com, the ransomware global attack volume increased by 151% for the first half of 2021 compared to the first half of 2020. Ransomware refers to the type of malware that encrypts files once inside an organization’s network. Once inside, the files are turned unusable along with the systems that rely on that information to run. This in turn enables malicious actors to demand a ransom in exchange for decryption.
In 2021, it’s not hard to see why ransomware has grown in popularity as the world continues operating largely on remote and hybrid working models. This shift has caused a spiral for traditional on-premises networks, and while IT and security teams have worked hard to ensure remote staff has access to the data and tools they need to perform their jobs, this updating and patching has caused vulnerabilities to grow in both size and complexity. Even cloud-based organizations face security challenges including misconfigurations and insufficient credential and access management.
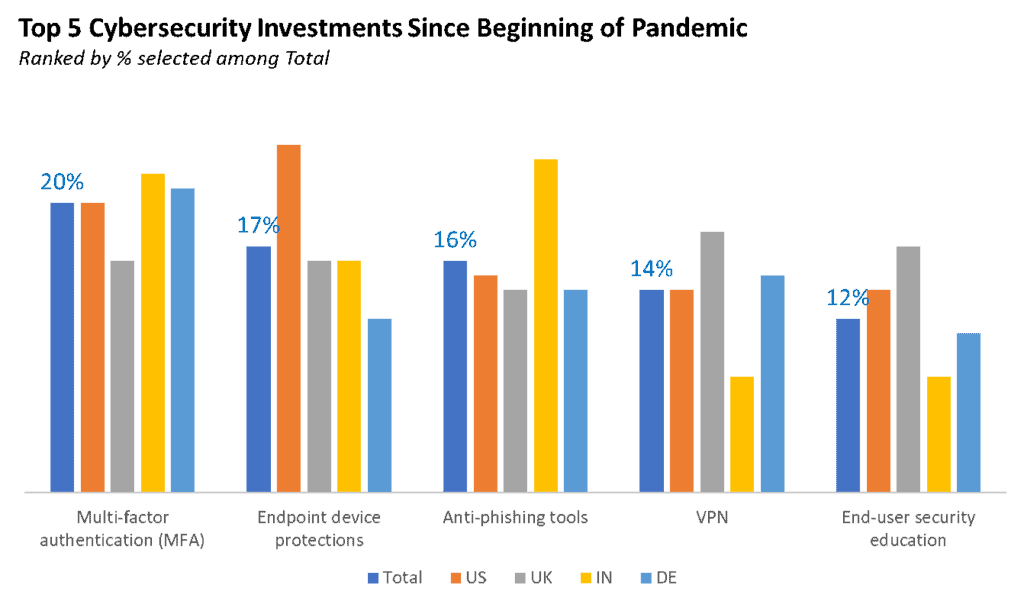
Enterprises need to work on creating a defined vulnerability program in order to best and most efficiently identify and mitigate all of these vulnerabilities described. In the end, understanding how cyber threats work and how to thwart them is critical to avoiding data breaches and protecting your company. From regularly enforcing password rules and updating operating systems and applications to implementing Virtual Private Networks (VPNs) and Multi-Factor Authentications (MFAs) or hiring third-party security system providers, now is the time to take investing in cybersecurity measures and leveraging the expertise of those recommended in the industry most seriously.
Now is the time to protect your business, your network, save money in the long run and avoid being the next costly cybersecurity/data breach victim.
Prime Data Centers doesn’t provide cybersecurity services, but we do advise leading enterprises on how their physical data center infrastructure factors into their broader business continuity/disaster recovery strategy. If we can help you in that regard, please reach out.






